The power industry is no stranger to cybersecurity. Given its essential role in every aspect of daily life, the industry follows strict guidelines for securing networks and devices that connen adopting new cybersecurity strategies and technologies.
With the rapid growth of renewable energy, a new set of challenges is emerging. The unique characteristics of renewable power generation infrastructure are creating a need for low-maintenance, highly reliable security technology on an unprecedented scale.
Securing operational technology
Before we look at what makes cybersecurity for renewables different, let’s look at what it has in common with security for other critical infrastructure operations.
The fundamental security considerations for renewable energy are similar to those of conventional power generation (and other critical infrastructure sectors, for that matter). The key principle is that critical infrastructure organizations need a significantly higher level of security, as evidenced by NERC CIP, Nuclear Regulatory Commission cybersecurity requirements, and other regulatory guidance.
Operational technology (OT) networks and devices need the best possible protection against cyber threats like ransomware because the consequences of a malware infection in an OT system are potentially severe, with widespread real-world consequences. In recent years we have seen how malware can cause gas shortages, for example, that disrupt life for hundreds of thousands of people.
In additions to protection against common cyber threats, OT systems also need protection against a second class of threats: hostile nations and other sophisticated groups who might launch cyber attacks directly against the devices that keep our electrical grid, fuel supply, and water systems operating.
Software-based firewalls: high cost, limited value
Traditional security measures like software-based firewalls are providing diminishing protection against advanced persistent threats. Firewalls run on commercial operating systems, and have rule-based security settings that may have inherent vulnerabilities. Firewalls can also be misconfigured or left in states that do not provide the expected level of security. Threat actors have access to libraries of ready-made attack techniques that can compromise firewalls and exploit rules that allow unintended access.
Organizations that depend on firewalls also have an ongoing need to keep their security software up to date, in an often useless attempt to stay ahead of new exploits and vulnerabilities. The result is an expensive, never-ending cycle of firewall updates that provide little value in return.
Air gaps: no longer a viable option
Another common approach to OT security is the air gap—a complete separation between critical OT systems and other networks. Since an air-gapped network can only be accessed by someone who is physically present at the facility, the systems within it are as safe as possible from external attack.
Air gaps create their own problems, however. Since remote access is not possible, routine tasks like updating and patching OT device software has to be done on site. This may not be an issue in a large plant with a full-time workforce, but routine maintenance becomes expensive and difficult when the systems are located at substations or other geographically remote, unstaffed facilities.
An even bigger issue is that air gaps trap important data, like device status and performance information, inside the system or network that generates it. This has become a critical business problem for many organizations now that cloud-based analytics solutions are widely available. Without a way to get data across an air gap and into a centralized database, organizations are unable to take advantage of the cost savings and performance enhancements that come from predictive maintenance, real-time device monitoring, and other activities that require OT-to-cloud connectivity.
Data diodes: hardware enforced security
To overcome the limitations of an air gap—without exposing critical systems to new risks—many organizations have turned to hardware-enforced security technology. Hardware-enforced security uses electrical components that function in predetermined ways and are not vulnerable to the attack techniques commonly used to bypass (or take over) software-based security solutions.
One of the most widely implemented hardware-enforced security solutions is the data diode—a device that uses “send only” and “receive only” electrical components to transfer data out of an air-gapped system or facility. Since the “send” and “receive” components cannot physically perform any other function, they cannot be used to send data backward into a protected network.
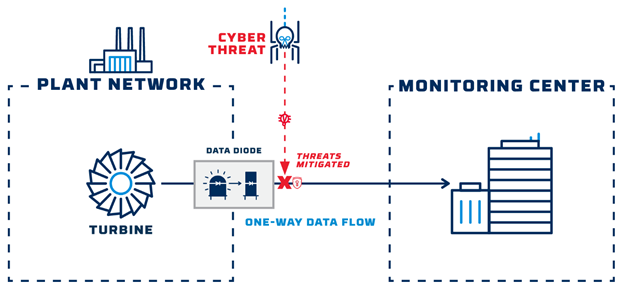
Unlike firewalls that depend on frequent software updates, data diodes can operate continuously for years with little to no maintenance, making them ideal for environments where taking systems offline would cause service disruptions or other unacceptable consequences.
Securing Renewable Energy Infrastructure
As mentioned above, renewable power generation systems have the same fundamental cybersecurity requirements as any other critical infrastructure system: OT devices need to be isolated to protect against malware that might migrate across from IT systems, and to protect against attacks that aim to disrupt OT operations directly.
However, renewable energy operations—wind and solar power generation in particular—have attributes that create an even more compelling need for OT-to-cloud connectivity and make hardware-enforced cybersecurity even more essential.
- Geographic isolation: Conventional power generation facilities are often located near urban centers, and have dozens or even hundreds of employees on site at all times. Renewable power generation, on the other hand, tends to happen in large, widely dispersed facilities, with few (or no) full-time employees on site.
- Device counts: Renewable energy also tends to involve more individual devices than conventional power generation. A gas-fired power plant, for example, might generate 500MW using two or three turbines. To generate the same amount of electricity, a wind farm might use 200 to 300 separate turbines.
- Natural fluctuations in output: As they depend on environmental conditions that are outside human control, renewable energy facility output cannot be predicted as precisely as conventional power generation.
Given these realities, energy companies face serious challenges in responding to maintenance needs or fluctuations in supply and demand without connecting their solar panels, wind turbines, and other OT equipment to the cloud. And without hardware-enforced cybersecurity, organizations risk exposing their devices to a wide range of cyber threats, along with ongoing costs to keep a large number of software-based firewalls up to date.
Hardware-enforced cybersecurity technology provides the ideal solution. With low-cost data diodes protecting each OT device, organizations can securely stream data to cloud-based services for real-time monitoring and analytics. Not only do data diodes provide maximum protection against cyber threats, they create little to no additional expense for ongoing maintenance.
As an example, a renewable energy operator recently implemented data diodes to transfer battery status, performance, and environmental data from its battery banks to a remote cloud storage environment for research and analytics.
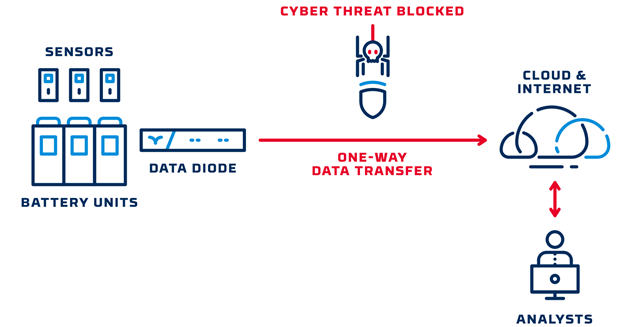
With this approach, the operator gained access to actionable, real-time data to enable performance optimization and energy trading, and maintained network segmentation to ensure maximum cyber threat protection for its assets. Similar implementations are becoming common as energy operators face the dual pressures of needing to extract essential data while avoiding threats to the systems that produce it.
Renewable energy generation is projected to grow exponentially in the coming decades. Hardware-enforced cybersecurity technology will help renewable energy reach its full potential, while minimizing risks to the infrastructure we all depend on.
To learn more about how hardware-enforced security can protect your organization’s critical assets, schedule a consultation with one of our cybersecurity experts today.