In today’s rapidly evolving cybersecurity landscape, government agencies face relentless pressure to protect sensitive information from increasingly sophisticated threats. Gone are the days when networks were confined to specific locations with clearly defined boundaries. The rise of cloud computing, mobile devices, and other endpoints has expanded these boundaries, creating a vast, interconnected portfolio of devices and networks—all essential to mission and operational readiness.
This shift demands a new approach to security, and Zero Trust Architecture (ZTA) has emerged as a key strategy in securing the networks of the U.S. Government. Zero Trust operates on the principle of “never trust, always verify.” Because Zero Trust deals so directly with ensuring access only where it is authorized and necessary, network segmentation is a critical component. By breaking down networks into smaller, isolated segments—each with its own ingress and egress controls—agencies can effectively limit unauthorized access and minimize the “blast radius” of potential breaches. This granular approach not only reduces the lateral movement of threats but also ensures that each segment is fortified with software and hardware-defined perimeters tailored to its specific security level and policy.
But why is network segmentation so crucial for government agencies, and how does it support the Zero Trust model?
Why Network Segmentation Matters in ZTA
In some ways, network segmentation could be viewed like compartments on a ship. If one compartment starts to flood, the others remain sealed off, preventing the entire ship from sinking. In the context of cybersecurity, this means that even if one segment of the network is compromised, the damage is contained and doesn’t spread to other parts of the network. This containment is vital for protecting sensitive government networks and data, where breaches can have catastrophic consequences.
Network segmentation augments ZTA in many ways, including:
- Improved Security: By isolating different parts of the network, agencies can better control access to sensitive data. This isolation makes it harder for attackers to move laterally within the network, thereby reducing the risk of widespread breaches.
- Enhanced Monitoring: Segmentation allows for more granular monitoring of network traffic. Agencies can set up specific rules and alerts for each segment, making it easier to detect and respond to suspicious activity.
- Regulatory Compliance: Many government agencies are subject to strict regulations regarding data handling and security. Network segmentation helps meet these requirements by ensuring that sensitive data is only accessible to those with the proper clearance.
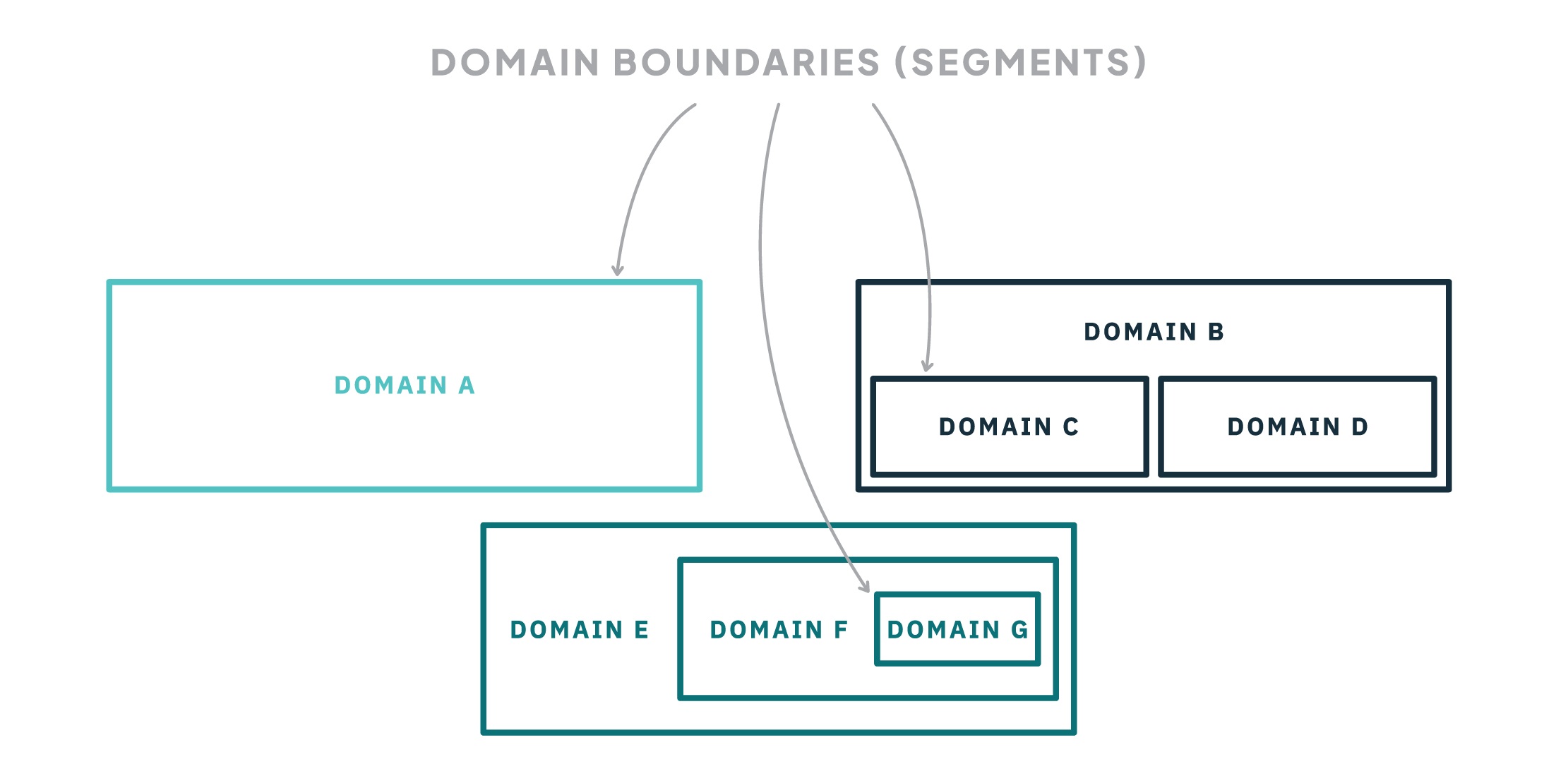
An illustration of a segmented network, showing isolated, compartmentalized domains.
Network Segmentation and Zero Trust
In a Zero Trust Architecture, the focus is on ensuring that every access or transfer request—whether it comes from inside or outside the network—is authenticated and authorized. Network segmentation plays a pivotal role in this process by enforcing boundaries around sensitive domains. Each of these boundaries provides an additional checkpoint to not only verify authorized access but also to create additional security zones and audit trails for threat or abnormal activity detection and forensics.
For example, consider a scenario where a threat actor gains access to a secure domain through a combination of social engineering and malware. Once on the network, the attacker is now limited in movement to other secure domains or subdomains and any attempts to access them are logged and potentially flagged as abnormal activity for threat detection.
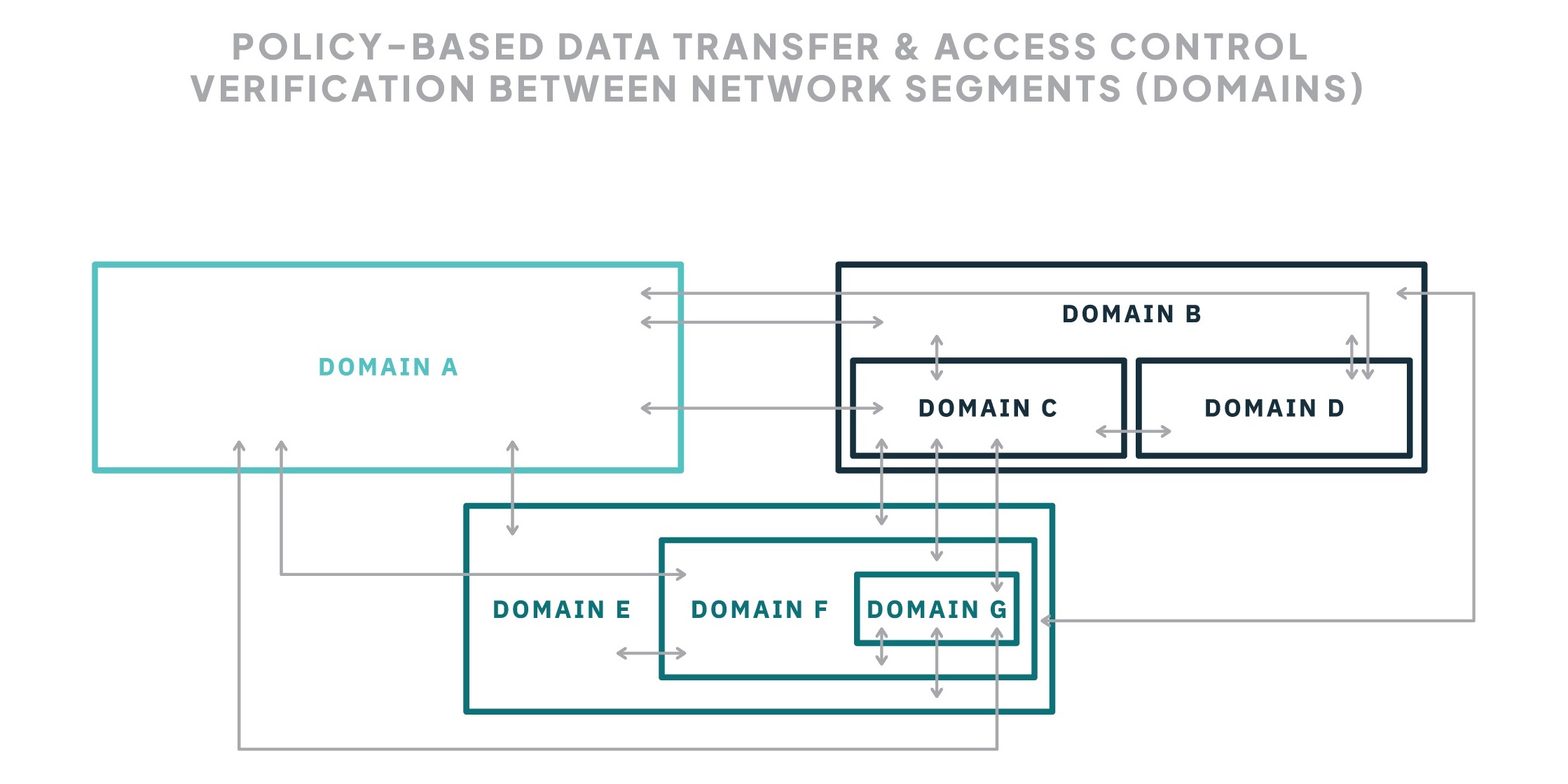
All connections between domains are controlled and monitored to ensure robust verification and logging according to ZTA policy.
How Owl Cyber Defense Supports Network Segmentation
Owl Cyber Defense cross domain solutions (CDS) and data diodes directly support network segmentation as part of a broader Zero Trust strategy. Solutions like Owl Talon and V2CDS, for example, enforce strict, policy-based data flow controls between network segments, providing security assurance and data confidentiality when data is transferred between domains, especially those of differing security levels. By implementing these types of solutions, agencies can ensure that their network segmentation strategies are robust, compliant, and capable of protecting against even the most sophisticated threats.
Additionally, because ZTA requires a layered, integrated approach, it is vital that network segmentation solutions are designed to interoperate seamlessly with other security tools, enhancing the overall effectiveness of network security. Whether it’s through content inspection and filtering, robust authentication mechanisms, or hardware-enforced one-way data transfer, Owl Cyber Defense provides a breadth of capabilities necessary to support highly-assured network segmentation within a ZTA framework.
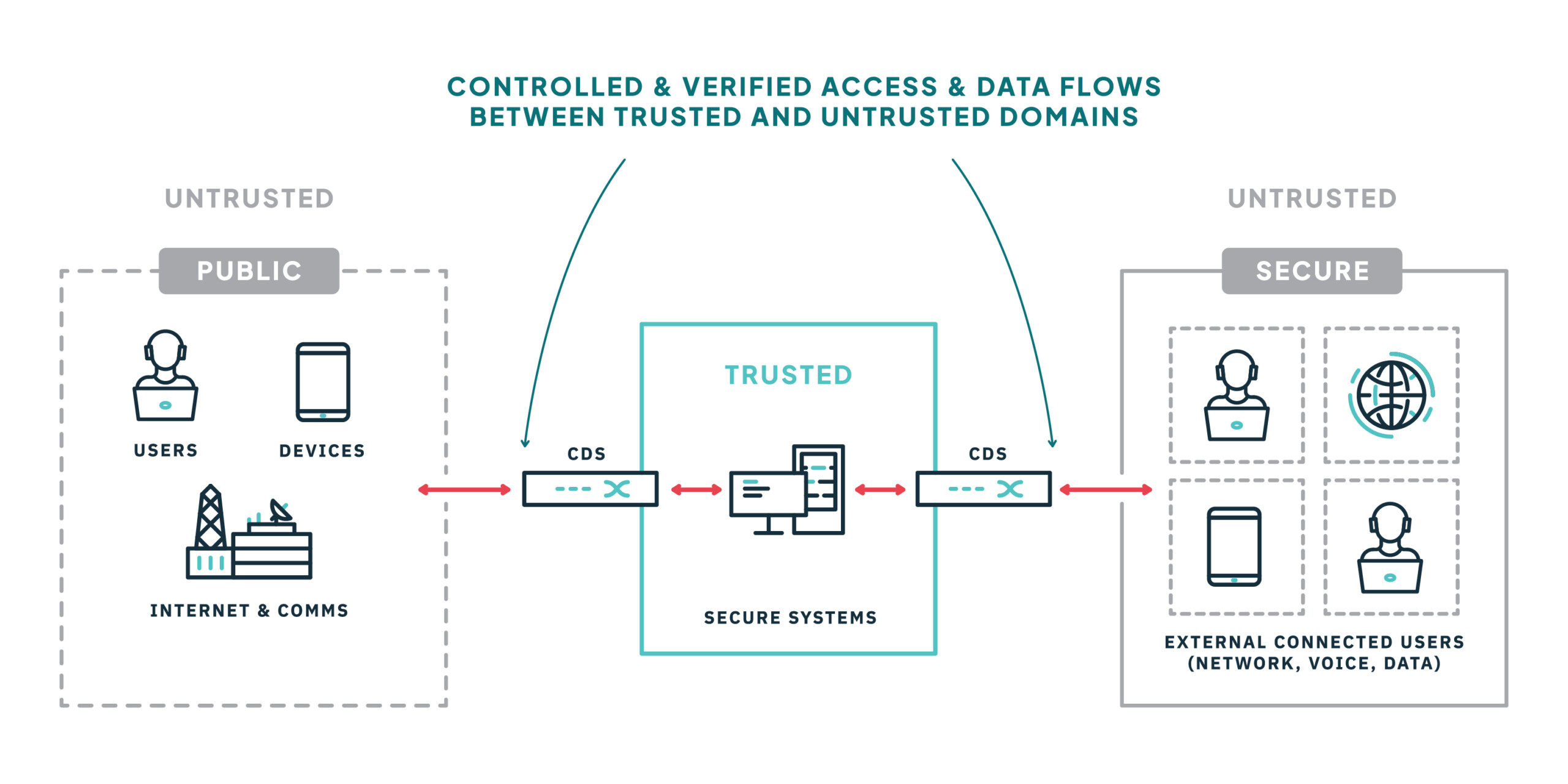
Owl Cyber Defense solutions address ZTA network segmentation principles with robust access and data flow controls.
What’s Next?
Network segmentation is a fundamental component of the Zero Trust model, especially within the networks of government agencies and other critical environments. By dividing and isolating domains, agencies can limit the spread of potential breaches, enhance monitoring, and ensure compliance with stringent security regulations.
Owl Cyber Defense, with its industry-leading solutions, provides the tools necessary to implement and maintain effective network segmentation. As agencies continue to adopt Zero Trust, leveraging the right technology partners will be key to ensuring that their networks remain secure and resilient in the face of evolving threats.
Learn more about cross domain solutions to address network segmentation and ZTA in our free ebook:




