For the U.S. Department of Defense, sharing real-time threat data with coalition partners is essential—but connecting to High Threat Networks (HTNs) exposes critical systems to advanced cyber risks. Our whitepaper explores strategies for enabling safe connectivity to HTNs, focusing on how agencies can ensure data protection, operational continuity, real-time threat response, and regulatory compliance.
Secure Data Sharing over High Threat Networks (HTN)
Sharing real-time threat data with coalition partners is essential—but connecting to High Threat Networks (HTNs) exposes critical systems to advanced cyber risks. By ensuring safe connectivity and data sharing to HTNs, agencies can realize real-time collaboration, data protection and regulatory compliance.
Get Started
Learn how to safely connect to and share data with risky, high threat networks.
Cybersecurity Challenge: Balancing Collaboration & Security with High Threat Networks

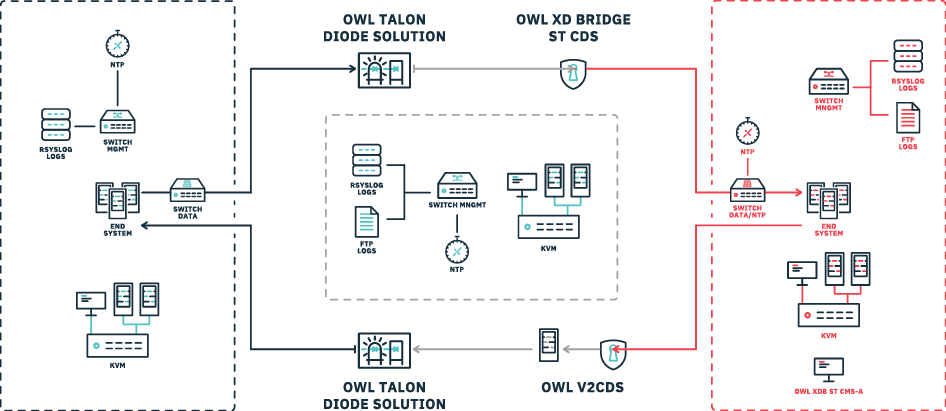
Owl’s Solution for HTN Connectivity & Collaboration
For unidirectional data transfer, information moves from the HTN through an Owl Talon PFD for a hardware-enforced break, then to the XD Bridge ST CDS for filtering before reaching the trusted network. For bidirectional transfer, after the initial unidirectional flow, data is processed by Owl’s V2CDS and passes through a second Talon PFD, ensuring secure, policy-controlled exchange back to the HTN.