What You Need to Know
Eleven critical vulnerabilities were found in a leading real-time operating system (RTOS) used in many industries, by leading vendors – VxWorks. The nature and scale of the vulnerability put many networks and operations at risk. Tools are in place to mitigate these vulnerabilities, but the numbers of devices suggest that not all will be patched, leaving potential opportunities for hackers to find.
“Since VxWorks is ordinarily used by the industrial and healthcare sectors, they are both put at an exceptionally severe risk by the URGENT/11 vulnerabilities. A compromised industrial controller could shut down a factory, and a pwned patient monitor could have a life threatening effect.”
— from
Hidden Time Bombs
My college chemistry professor told us a story of how, when cleaning out a storage closet under the auditorium, the chemistry department found large vats of old hydrogen peroxide. The problem was, hydrogen peroxide becomes explosive as it ages. And these vats were quite old. Needless to say, they had to call in a bomb squad to take the peroxide away. The lesson is the danger of explosion was always there, and increasing daily, even though no one had found it out.
VxWorks is a widely used RTOS that has been in use for over 30 years. It can be found in over 2 billion devices – everything from industrial controllers and SCADA systems, to robots, networking devices, medical devices, cars, planes, and even spacecraft.
Yes. Pretty much everywhere.
The URGENT/11
This omnipresence became all the more troubling when a cybersecurity company, Armis, last year published a study that listed 11 critical vulnerabilities (dubbed the URGENT/11) in VxWorks.
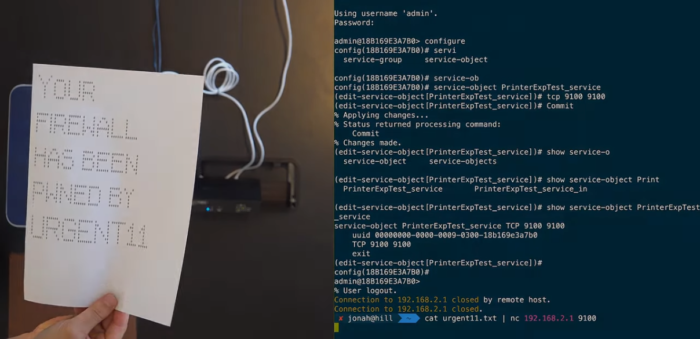
One example they chose was around the SonicWall firewall (one estimate uncovered over 800 thousand SonicWall firewalls connected to the open internet). In Armis’ exploit example, they run a script that uses an URGENT/11 vulnerability to overcome the firewall and gain access to the network behind it, printing out something on a networked printer that was supposed to be secured (see image below).
Like the hydrogen peroxide, VxWorks was always in danger of an explosion. Good thing someone discovered it and we can call in the bomb squad: vendors are providing fixes for the problem. Armis even has software to uncover any vulnerable devices.
What to Do?
But with millions of devices running VxWorks, and some in critical operations, will they all actually get updated? Providing the patch doesn’t mean organizations can or will apply it – or that they will even know about it. So how do we ensure other unknown vulnerabilities don’t become unknown bombs on your network?
Think for a moment: These VxWorks vulnerabilities have been around for at least 13 years waiting on someone to find them. Also, it’s not just legacy devices – this was in the latest release.
The environment will always shift – devices and networks get more interconnected, new exploits are discovered, vulnerabilities are introduced by users or via changes in the software. How might we design our networks to future-proof our trusty devices from becoming a time bomb we don’t know about until it is too late?
The lesson I get from the URGENT/11 is that we need new ways to secure our devices, especially in the face of new vulnerabilities and pressures against timely updating and patching.
How are you addressing the URGENT/11? How do you secure and future-proof your legacy devices?
One Last Thing
If you want to keep up on cybersecurity issues in pharma manufacturing, subscribe below to my bi-weekly newsletter with links and commentary on the main stories of the moment.



