Cryptocurrency exchanges and custodians are an emerging and rapidly expanding market (>25%), with growth far exceeding that of the traditional capital markets sector. A relatively new market that first appeared in 2011, today there are over 250 crypto-asset exchanges worldwide.
However, the combination of complex new crypto technology and aggressive growth has led to subpar cybersecurity policies and implementations in crypto businesses. While traditional banks, brokers, and exchanges have had decades to develop and mature their cybersecurity practices, crypto is has rested on its laurels as a “secure technology.” As one might expect, this hubris has led to a number of successful cyberattacks and blunders on cryptocurrency exchanges. Mt. Gox, Coincheck, Iota, Bancor, and Bitfinex are just a handful of example firms of many that have stumbled in this area.
Unfortunately, some of the same aspects that make crypto secure also make it more difficult to protect. The decentralized trust property that makes blockchain models secure and efficient can also penalize participants for security mistakes – instantly and permanently. A distributed ledger is a dispassionate judge of ownership – there is no central authority to hear complaints and right wrongs. For this reason, regulators are moving slowly on security tokenization as a financial innovation, even when they understand the technology and appreciate the efficiencies. What if something goes wrong? Who can the regulator hold responsible? One cannot undo a crypto heist… when crypto assets (digital keys) are transferred and verified, there is generally no recourse for the victim.

Firms that control crypto assets generally keep private keys in “hot wallets” – meaning the assets are available to transact on their platform network – or in “cold wallets” which are stored offline. Hot wallet networks are generally protected by firewalls, and the cold wallet networks simply pull the plug – they are offline and air-gapped to the rest of the world.
Each of these approaches to storing crypto keys has its benefits but also presents challenges. The connected network is highly available, but only as safe as its firewall, which is subject to known and unknown software vulnerabilities, and administrative misconfiguration. The disconnected network is highly secure, but well… disconnected. Getting keys back online requires time to move them, and the air gap prevents communication of important alerts out of the network.
Fortunately, there is a solution, borrowed from government intelligence agencies and critical infrastructure operators, that represents the best of both of these solutions: one-way-only data flows enforced by data diodes.
Data diodes are hardware-enforced network devices that provide one-way data transfers between networks. They use optical separation to transmit data across an air gap, and their hardware configuration makes sending data in the opposite direction physically impossible.
You might be wondering how that works if an acknowledgement is needed from the other side, for example, in the case of a TCP/IP connection. The answer, in Owl’s case, is built-in, specially designed proxy servers provide endpoints for communications into and out of the data diode. These proxy servers can handle numerous protocols and multiple simultaneous data streams for data transmission, file transfer, database replication, etc.
With this technology, data can pass between two networks without an open connection, handshaking, or knowing anything about the existence of each other. This enables safer, more secure network architectures, as illustrated below:
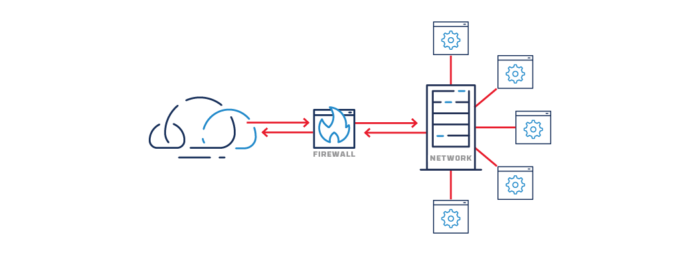
Common firewall network protection
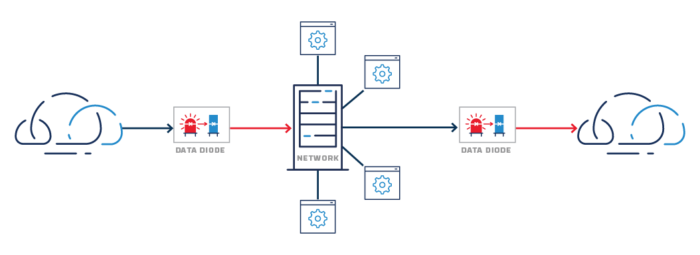
More secure one-way link network protection
For crypto asset custodians and exchanges, data diodes can be used to safely monitor equipment inside air-gapped cold storage vaults, get alerts and events to a Security Operations Center, improve speed to retrieve keys from cold storage, and create secure processing enclaves for trading and transacting customer orders.
For example: when software needs to process private keys in their unencrypted state (aka “in the clear”), malware could spy on the keys in memory, communicate details outside the network, and lead to disaster. Separate paths into and out of the processing network create a challenge for would-be attackers because one-way links cannot be used for a conventional two-way socket connection. The network cannot be pinged or probed, and malware cannot “phone home” back to potential attackers. Intrusion and command/control attempts are thereby thwarted.
It’s also worth noting that data diodes can even help to limit risk from insider attacks (something that crypto exchanges are familiar with) because the one-way property cannot be changed. Configuring data to flow through the device also requires cooperation between administrators on both the sending and receiving networks.
So how are you securing your secure processing network? We would love to hear your thoughts, please contact us using the Contact button at the top or bottom of the page.




