The vulnerabilities inherent in software-based cybersecurity solutions cause greater concern every year. Due to the fact that any software-based solution relies on a central processing unit (CPU) for its operation—and a typical CPU has no built-in restrictions that prevent the execution of malicious code—software-based security is vulnerable to a constantly-growing number of exploits and attack methods.
The threat is not merely theoretical. The perpetual stream of CERT advisories and constant pressure to update and patch systems including firewalls is evidence that a software-based approach to security depends on a constant stream of updates to patch and repair newly discovered vulnerabilities. The recently uncovered Ripple20 and Amnesia:33 attacks provide concrete examples of the threats lurking in widely-deployed software stacks.
Hardware-based cybersecurity using field programmable gate array (FPGA) technology provides stronger, more cost effective protection for devices used by critical infrastructure, military, and intelligence organizations. Unlike the CPUs that power software firewalls, FPGAs are limited to a finite number of possible states, greatly reducing the scope of potential implementation flaws or vulnerabilities.
FPGA security in action
A basic architecture for a secure FPGA filter is shown below. In this design, an independent administrative processor has been added. Only the administrative CPU has access to the interface on the FPGA to load a new configuration file. This processor must be isolated from the primary data path to ensure that a malicious attacker cannot gain access to the configuration port. In many cases, it is isolated from all network access, requiring physical access to the system to deliver an update.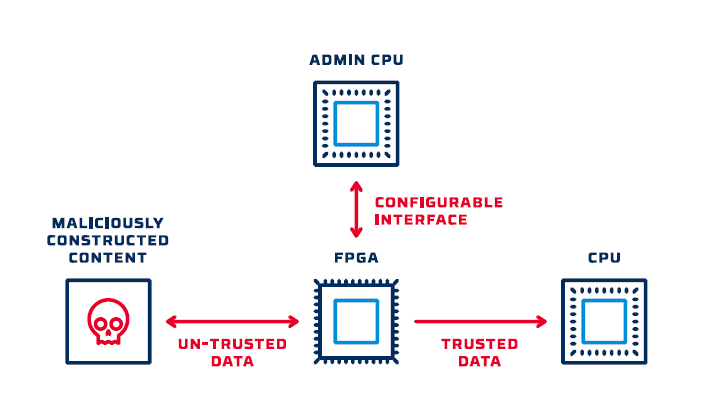
Additionally, most modern FPGAs can be configured to only accept a digitally signed configuration file. If the secret key needed to sign a new configuration is external to the admin CPU then even with access to this segmented processor an attacker can still not change the configuration of the FPGA.
When hardware-based filtering is implemented using this model, organizations can achieve a level of security that far exceeds what a software-based firewall can provide. However, developing FPGA filters is also much more complex than the creation of software filters that run on a CPU. Here’s a quick look at some development techniques that accelerate the process and make practical, FPGA-based security a reality.
Modular approach
The use of reliable, thoroughly tested functional modules greatly accelerates the process of developing new hardware-based filters. This allows for re-use of filter logic for common data types and reduces the amount of custom development needed to validate a new protocol.
Data normalization
Data normalization is another technique that can greatly improve the effectiveness of hardware-based data validation and enforcement. As shown below, software running in the support CPU is used to pre-process protocol-specific messages and handle complex, stateful conditions.
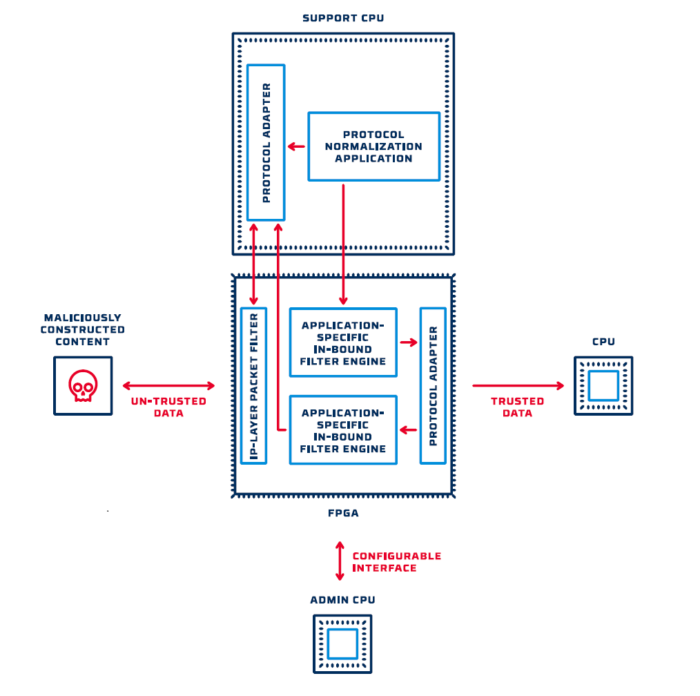
Data that is sent to the FPGA has been tagged and normalized so that the FPGA filter engine can enforce the appropriate policy and then recombine the data into a conventional wire-level representation.
Tool chains vs. custom code
Rather than develop custom code to implement a new protocol filter, it is far more efficient to create a tool chain that configures mature, modular functions into a custom deployment image. Inputs to the tool chain are a set of pre-defined functions, the protocol specification, and an application-specific policy. The policy defines what specific properties and values of the protocol will be tested and enforced by the filter. For example, if the protocol in question is MODBUS, the policy might specify that only a subset of valid MODBUS message types shall be supported, and data value or range values must be enforced.
Application-specific protocol and content enforcement
Firewall technology has evolved significantly in an attempt to protect vulnerable systems against continually evolving threats. The most advanced firewalls (sometimes called a next-generation firewall or NGFW) have targeted rules that apply to a specific application and data type. By implementing protocol filters that recognize common network applications, these devices allow network security architects to develop rules that are context aware and limit traffic to only the type of activity that is expected on a network segment.
Hardware-enforced security platforms can also be configured to apply application-specific policies. By using a mature tool chain to automate the process of generating an application-specific filter implementation, it is practical to develop custom filter instances for each network segment that requires protection. The benefit of this approach is that vulnerable systems can be protected from any network traffic that does not conform to narrowly defined, white-listed message content.