Until something even worse comes along, the Log4j remote code execution vulnerability will be the biggest story (and biggest headache) in cybersecurity. But even as security teams around the world work to identify and patch the hundreds of millions of devices that have the Log4j vulnerability, new threats will continue to emerge.
Like Log4j, and Amnesia:33 and Ripple20 before it (and hundreds of others before those), many of tomorrow’s threats will center around zero-day vulnerabilities–previously unknown software flaws that threat actors can exploit immediately, leaving no time for organizations to prepare before an attack.
Zero-day vulnerabilities are a major concern for any organization, but for critical infrastructure operations like power plants, oil and gas pipelines, or transportation systems, the stakes are even higher. Successful attacks against these targets can disrupt daily life for millions of people, with the potential for widespread physical damage.
This raises an obvious question: how can organizations protect themselves against attacks that (by definition) they know nothing about and can’t predict?
The answer is to defend critical systems with hardware-enforced security solutions that include data diodes to control the flow of data.
Unlike firewalls or other software-based security solutions, hardware-enforced technology provides reliable protection against zero-day attacks, because data diodes block threat actors from establishing communication with vulnerable systems in the first place. Without the ability to send malicious commands to targeted systems, hackers can’t exploit any weaknesses that might exist, even if the would-be victims are unaware of the vulnerabilities themselves.
The Log4j remote code execution vulnerability provides a perfect example.
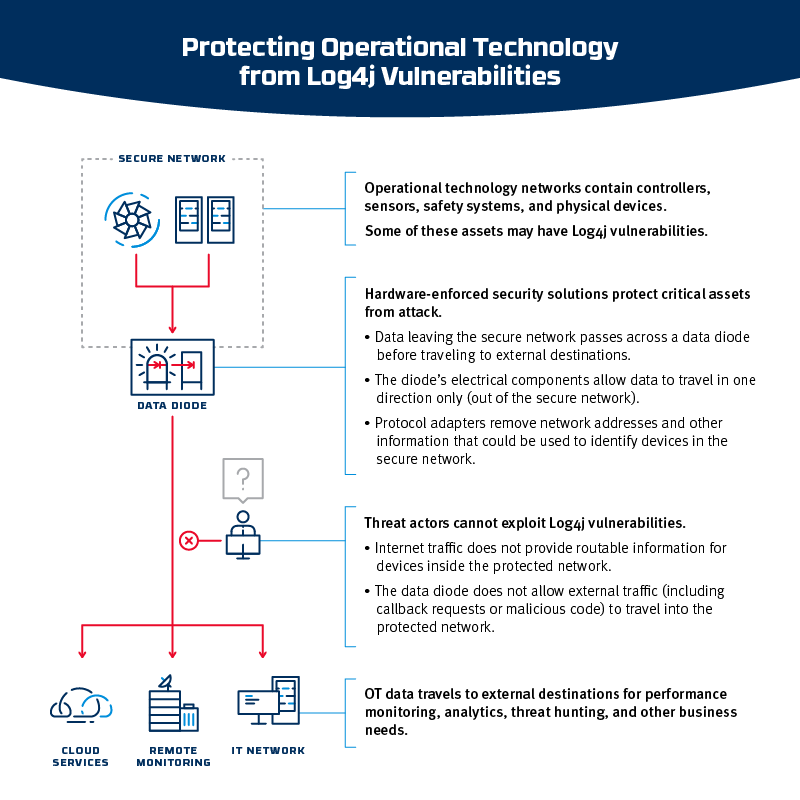
Operational technology (OT) networks contain a wide range of sensitive assets like controllers, sensors, and safety systems, some of which may have the Log4j vulnerability. But when an OT network is protected by a hardware-enforced security solution, data leaving the secure network passes across a data diode before traveling to external destinations. The diode’s electrical components allow data to travel in one direction only (out of the secure network), while protocol adapters remove network addresses and other information that could be used to identify devices in the secure network.
With a data diode in place, OT data can travel to external destinations for performance monitoring, analytics, threat hunting, and other business needs, but threat actors cannot send data in to exploit vulnerabilities like Log4j or Ripple20. And when a new zero-day vulnerability is discovered, threat actors will remain unable to attack the network.
Organizations around the globe rely on Owl data diodes to protect their critical systems from known and unknown cyber threats today. To learn more about how Owl can help your organization, schedule a consultation with one of our experts today.