Cloud connectivity offers a wealth of benefits for energy providers and other critical infrastructure operators. Sending data from operational technology devices to the cloud allows asset owners to use remote diagnostic and analysis tools, improve supply chain management, and take advantage of enhanced services from machine vendors and other providers.
New connections, however, can introduce new risks. Inadequately secured connections create opportunities for unauthorized parties to access critical systems, and some security “solutions” have the potential to be hijacked and used to launch attacks by sophisticated threat actors.
The complex dynamics of evolving threats and maturing cloud capabilities have led to a variety of security postures in the energy industry and the critical infrastructure sector in general. Most of today’s scenarios fall into one of four categories, several of which might exist simultaneously within a single organization:
- No cloud connectivity: many organizations, particularly within the power generation industry, prohibit any external connectivity for OT devices.
- Purdue Model connectivity: organizations that strictly follow the Purdue Model for industrial control systems typically route sensor data through multiple OT and IT layers before sending it to the cloud.
- Direct connectivity with software-based controls: rather than routing data through a complex Purdue Model architecture, some organizations connect OT devices directly to the cloud, using software-based firewalls to secure the connections.
- Direct connectivity with no organizational control: some organizations are discovering that their industrial devices are “phoning home” on their own, using embedded cellular or Wi-Fi capabilities that the asset owners did not know existed.
Each of these approaches to connectivity involves a compromise in operational effectiveness or security (or in some cases, both at once). There is, however, another approach to cloud connectivity that enables organizations to enjoy the key benefits of cloud computing, while maintaining the highest possible level of security for critical networks and devices:
- Air-gapped edge gateways: the best long-term approach to cloud connectivity is to stream OT data directly to the cloud, using hardware-enforced security technology to exercise strict control over the direction and content of data flows. Hardware-based security eliminates the vulnerabilities inherent in software-based solutions, and enables complete control over the flow of data from the device to the cloud.
Hardware enforced security
Air-gapped edge gateways use data diodes to enforce a deterministic one-way data flow, providing no possible path for data to flow backward to the connected device.
Inside a data diode, information travels between hardware components that are capable of sending data in only one direction. The components can be pairs of optical transmitters and receivers, digital isolators, or equivalent technology.
Transmission protocols are terminated on the “send” side of a data diode, and only the packet payload is transferred to the “receive” side. On the “receive” side, a new protocol session is established. This design allows for one-way transmission using protocols that are inherently two-way, while concealing MAC addresses and other send-side network information.
In addition to enforcing one-way data flow, air-gapped edge gateways can perform application- and protocol-specific filtering and validation to ensure that only authorized data is transmitted from the facility to the cloud.
Air-gapped edge gateways are widely used within the energy sector today and provide an effective solution for organizations that need to maintain maximum security while sending data out of the OT network. Advanced gateways include the capability to load data directly into popular cloud services such as AWS, Azure, and Google Cloud without the need for an additional external proxy. This includes the ability to perform mutual certificate-based authentication and TLS session management directly in the destination proxy server.
Edge gateway technology has become even more efficient and cost-effective in recent years, thanks to low-cost gateway appliances that provide reliable, low-maintenance data diode functionality. In addition, the technology now exists to embed hardware-enforced security technology directly into OT devices. The next generation of industrial devices and sensors will include embedded data diodes that allow asset owners to control the flow of data through wireless, cellular, or wired connections to the cloud.
Secure design patterns for industrial IoT
There are several proven designs for using air-gapped edge gateways to enable OT-to-cloud connectivity. Solution designs depend primarily on the type of sensor that is producing the data.
Some sensors are integrated into the machine controller, while others are external–either bolted on to the exterior of the device (for example, a vibration sensor) or placed nearby (like a video camera or temperature sensor).
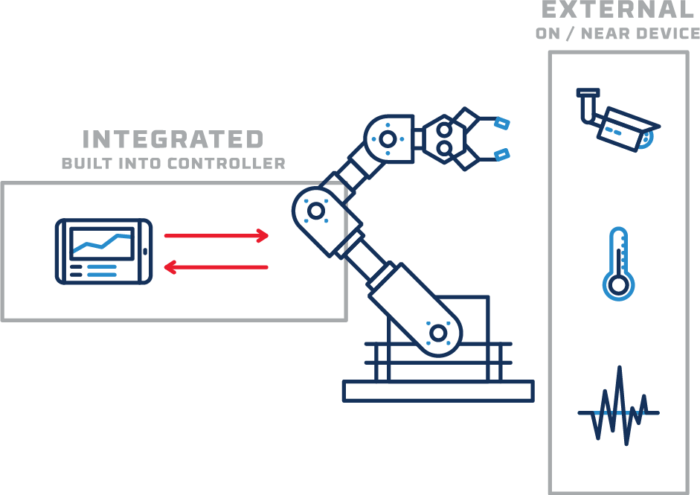
When possible, data flows from external and internal sensors should be isolated from each other. Maintaining this isolation can be difficult or impossible when data has to travel through the entire OT and IT network on its way to the cloud. But with direct OT-to-cloud connections–secured through hardware-enforced one-way transfer–organizations can keep their data flows as simple and secure as possible.
Below are a few of the most common use cases and solution designs for edge gateway technology.
Design pattern: Isolated external sensors
Sending data from external sensors to the cloud is one of the most straightforward implementations of edge gateway technology. As depicted below, multiple external sensors are often deployed to monitor different conditions of a single OT asset–for example, a vibration sensor, a temperature sensor, and a video camera might all be arrayed on or near an industrial machine. Routing the data from each of those sensors through a Purdue-model architecture would be time-consuming and complex, and would create multiple opportunities for misconfiguration. A simpler, more secure approach is to stream the data directly to the cloud.
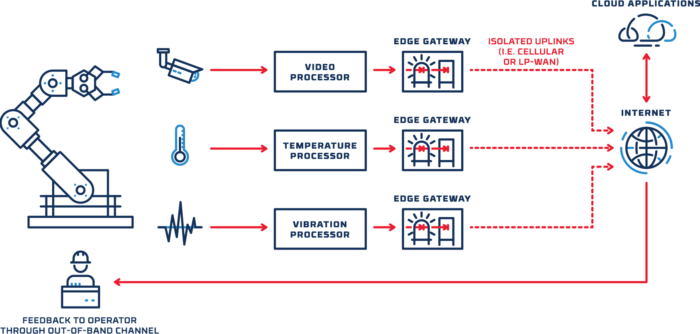
With this design, organizations can gain the benefits of cloud-based analytics and monitoring, with no need to provide a local connection for external sensors.
Design pattern: integrated sensors
In other cases, sensors and data processing functions are integrated into device controllers that are connected directly to the local OT network. For example, a machine controller might include a sensor that monitors the speed or position of an element within the machine. Many organizations might hesitate to enable a connection between the controller and the cloud, out of concern that a threat actor could use the connection to gain access to the device or the local network. This risk can be managed by using a separate port on the controller to send sensor data across a diode and out to the cloud. The machine controller’s existing connection to the local OT network is unchanged, and the data diode precludes any possibility that data could be sent from the cloud back to the controller.
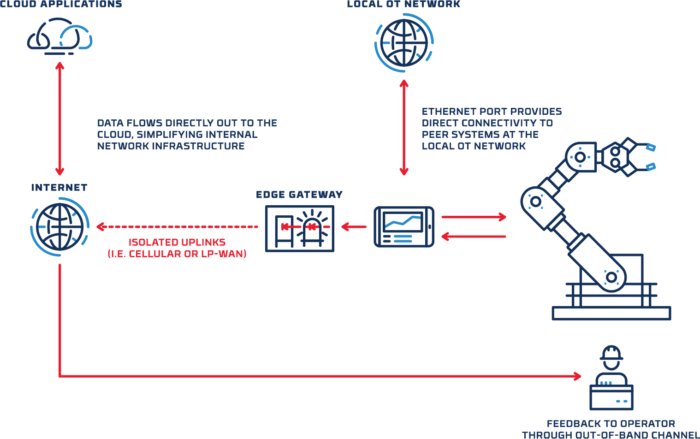
In addition to providing a deterministic one-way data flow, the gateway can also be configured to perform protocol validation and filtering, enabling complete organizational control over the flow of OT data to the cloud.
Design pattern: database replication
A common variation on the “integrated sensor” use case involves replicating OT historian data in the cloud. In this case, sensor data is streamed to a local historian database, and then the database contents are replicated to the cloud after passing across a data diode. Here again, the machine controller’s connection to the local OT network is unaffected, and there is no possibility that a threat actor could send data backward across the gateway.
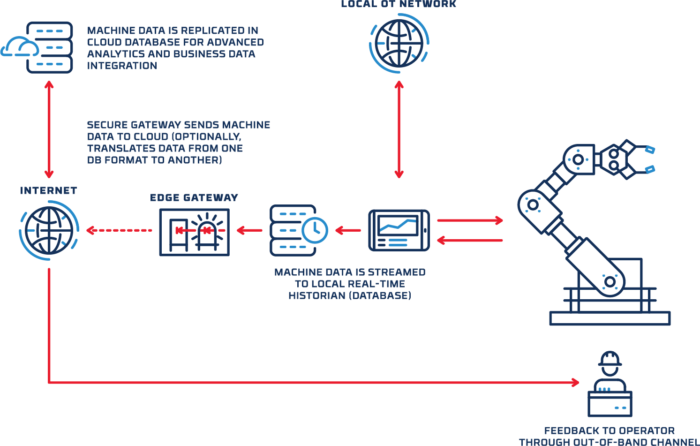
Along with protocol validation and filtering, the gateway can be configured to convert data into a different database format before streaming it to the cloud.
Building a new paradigm
Cloud-connected OT devices break traditional OT security models. The rapid proliferation of smart industrial devices requires a new paradigm for connectivity and security, based on data flow control and application-aware protocol enforcement. Air-gapped edge gateway technology, implemented according to proven design patterns, provides a path forward for maximizing OT performance and efficiency while minimizing risk.
To learn more about Owl’s solutions for cloud connectivity, including supported platforms and protocols, plus examples of recent customer implementations, read our new brochure Securing OT & IIoT Connections to the Cloud.



