I recently wrote a post about how IIoT devices are upending the Purdue Model as folks jump layers and stream data from the low layers directly up to the higher layers and beyond. Thinking about this some more, I feel that IIoT isn’t upending the Purdue Model, it’s bypassing it. That is, trying to cram the IIoT into the Purdue Model is perhaps not the way to go. Rather, we should just go around it.
Allow me to elaborate.
Not Just Upended, Bypassed
The Purdue Model was designed a long time ago as a framework for digitization of manufacturing. The kinds of networks, computing devices, and data streams back then were well suited to a layered, structured model for OT and IT networks.
The Purdue Model’s security was built OT-IT separation, with each layer doing its thing and sending data to the next layer up. It was divided up based on corporate functions, but also the basic, gated security controls that had traditionally been used to keep OT systems separate and secure from more exposed or untrusted networks (and the internet).
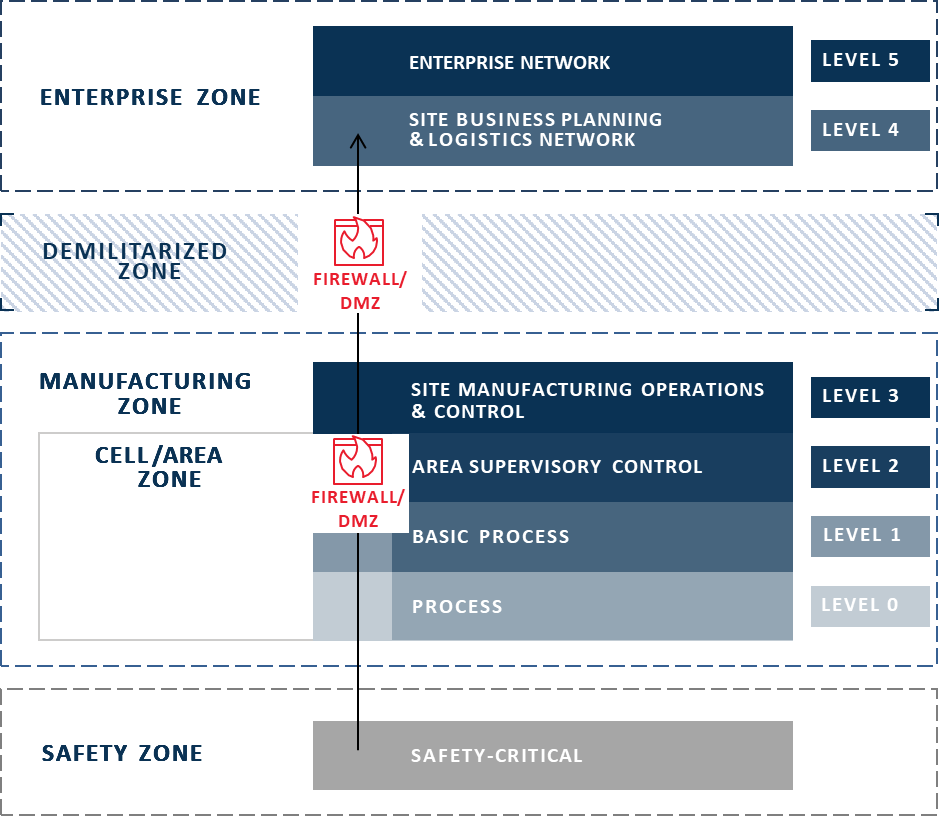
Basic Gated Data Transfer Model
But in the IIoT, OT-IT separation is no longer valid, and internet and cloud connectivity are basic staples, if not requirements. Endpoints are spread out across machines, networks, user devices, organizations (for example, cloud vendors, third-party asset owners, and contract manufacturers). Data is being pushed out of the entire organization from Level 5 all the way down to devices attached to machines at Level 0, like vibration sensors smart enough to know when to do something or send an alert (rather than sending all the info to Layer 3 to be analyzed and acted upon).
This paradigm shift calls for a new approach – one that won’t fit in the layered, structured model – but all that legacy infrastructure in manufacturing isn’t just going to *POOF* disappear overnight. So, we can’t just throw out the old model. We’re better off building a new framework above and beyond the traditional model. As I mentioned in my previous post, this new “superstructure” of the model includes a Level 6, above the traditional Purdue Model, in the Cloud/Internet Zone, and a parallel IIoT Zone outside the traditional Zones where IIoT systems and devices across all OT and IT Zones connect independently to the cloud.
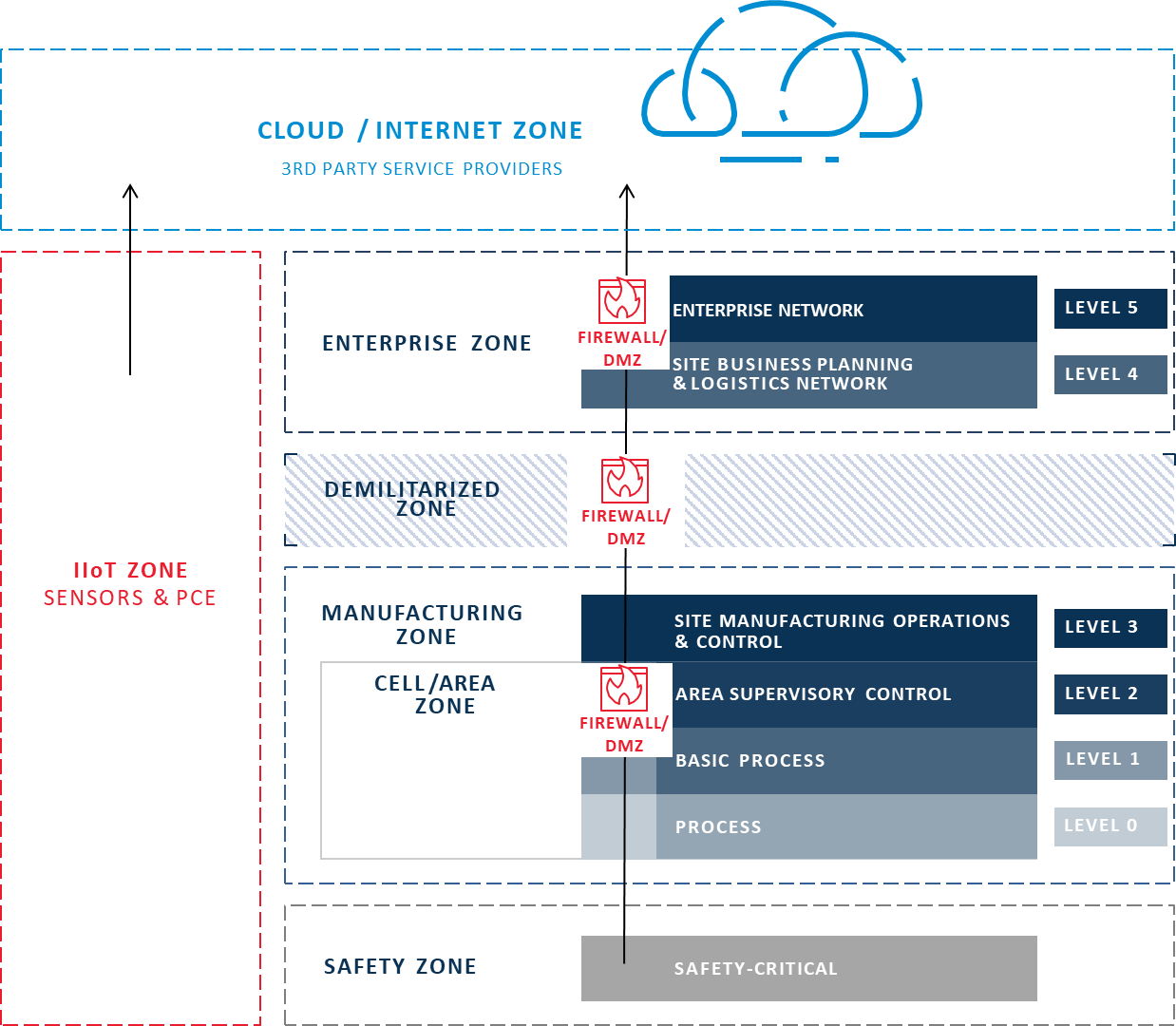
Proposed New IIoT Purdue Model
None of the IIoT endpoints, sensors, or devices care if they are OT or IT or what Layers they are on. They’ve all got jobs to do and we need to connect them to the infrastructure they need to do their jobs – to get data to the systems and users that need it – while keeping secure the devices and endpoints themselves, and by proxy, their underlying systems and equipment.
Perimeter for One
Most organizations traditionally use the OT-IT split as a demarcation line for perimeter defenses – who and what goes where is determined largely by a broader boundary around each Zone, with specific paths in and out of Zones guarded via firewalls within DMZs. This strategy places a single point of failure both for the security of the Zones and for the traffic traveling between them.
In contrast, in the IIoT world, folks would rather not depend on a single checkpoint to demarcate and defend a large zone. Instead, they’re looking for simple, inexpensive, and easy-to-manage security solutions that can secure each individual IIoT asset or data stream.
Any security failure in this new IIoT model is localized to a perimeter of one, rather than putting all the other devices at risk. If anything goes wrong, it’s only for that asset or stream, not a whole production network requiring thousands of dollars of effort to get back into a secure state, not to mention losing visibility to all of the machines behind that single connection. Failure is also more easily addressed without having to worry about other assets or in-depth troubleshooting and diagnostics.
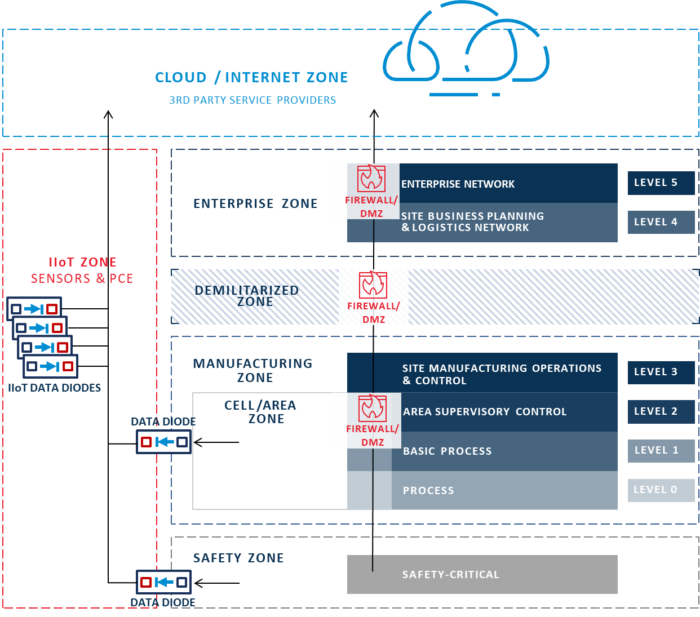
Proposed New IIoT Data Sharing Model
Connect More, Securely
In summary, this usage of IIoT devices needs a whole new way of thinking about security. We are already seeing various markets shift to this new model for endpoint management, awareness, and security. Hardware-enforced security solutions, such as Owl data diodes, are well positioned to meet the complex challenges of IIoT devices and increased connectivity and will be even more important to keep down the complexity to security ratio.
As a parting thought: I keep thinking of the manufacturers I speak with who are not digitized enough to have a fully formed Purdue Model for their networks. I’m no longer convinced that we need to push them into a Purdue Model of thinking. Indeed, by going straight to the IIoT model, instead of building perimeter defenses and layers of networks, they can leap-frog straight into a distributed and micro-segmented superstructure outside of the traditional Purdue Model.
What do you think?




